Vendors & Servıces
SafeDash
At Safedash, we are unwavering in our commitment to fortifying your digital landscape against an array of cyber threats.
Flagship Products
At Safedash, we are unwavering in our commitment to fortifying your digital landscape against an array of cyber threats. We understand that in today’s dynamic digital environment, businesses face ever-growing challenges that require resilient and adaptable solutions. Our two flagship products, CastDDOS and CastLOAD, are specifically designed to ensure your business remains robust and agile in the face of unexpected digital adversities.
Why Safedash CastDDOS & CastLOAD
Investing in load and ddos testing is an investment in your product's quality, user experience, and reliability. A successful DDoS and LOAD testing aims to uncover the organization's cyber security posture.

Cloud Based
2000+ Nodes and up to 700 Gbps traffic

Comprehensive
150+ Pre-Defined Tests

Geographically diverse:
White-listed DDoS attack traffic all the way to end customer from 11 regions

Agile
System designed to be scaled up or down very quickly

Bespoke
All attack types and scripts developed in house by CAST DDoS and can be modified very easily according to customer requests

User Friendly
Very easy to start the attack on one click and get report immediately
Engage with Safedash
Our team of experts is ready to support you in enhancing your digital resilience and navigating the complexities of cyber threats with confidence.
Don't let unexpected traffic surges bring your system down. Schedule a load test with CastLOAD today to fortify your platform's performance, ensuring agility and dependability. Our experts are ready to support you in enhancing your digital resilience and navigating cyber threats confidently.
Safedash is a beacon of excellence in the cybersecurity landscape. Our mission to empower businesses, combined with our unwavering commitment to security, innovation, and customer success, positions us as your trusted partner. Collaborate with us and benefit from our expertise and dedication.
Join Safedash and protect your digital infrastructure with our flagship products, CastDDOS and CastLOAD. These tools are designed to safeguard and enhance your systems, ensuring your business thrives amidst ever-evolving cyber threats. Secure your growth and success in the digital age with Safedash.
CAST DDoS | CAST LOAD
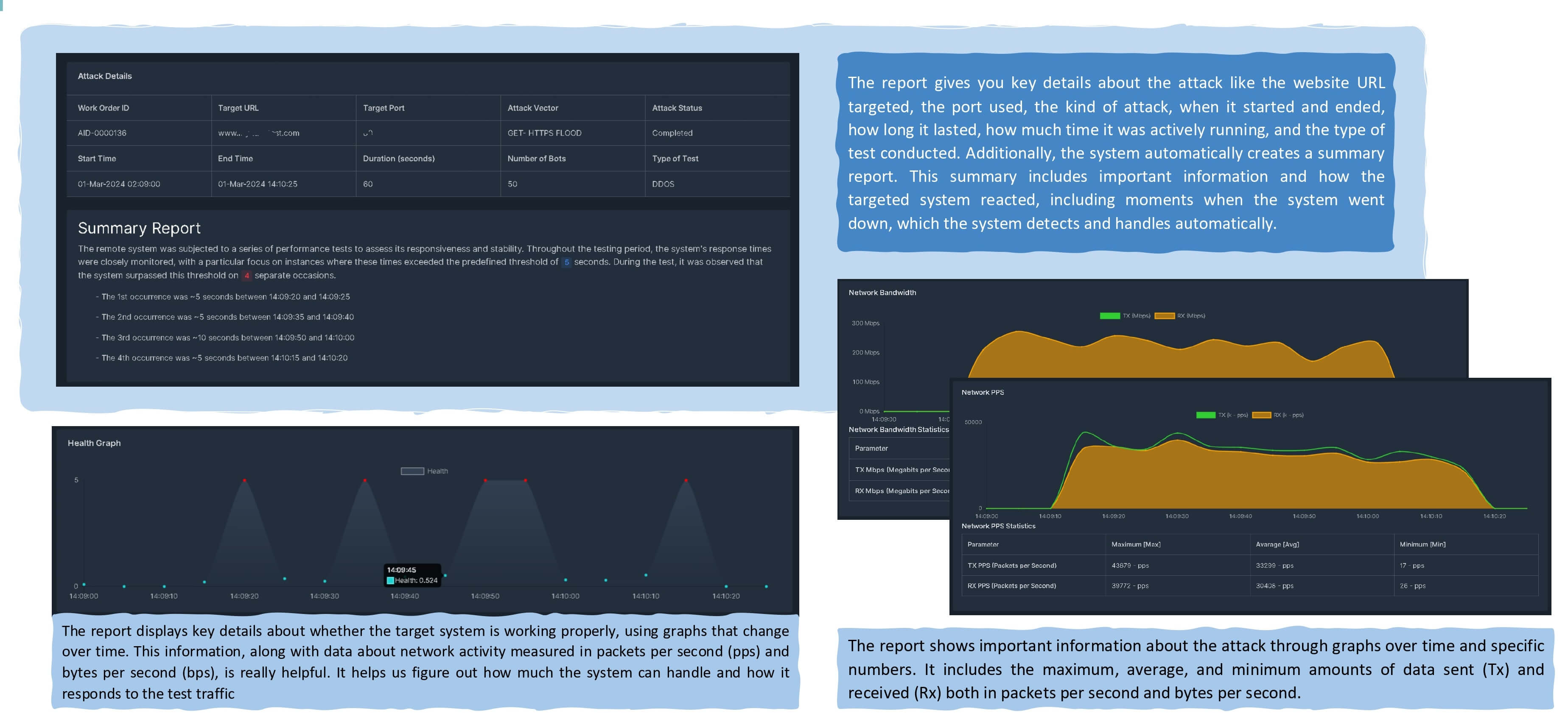
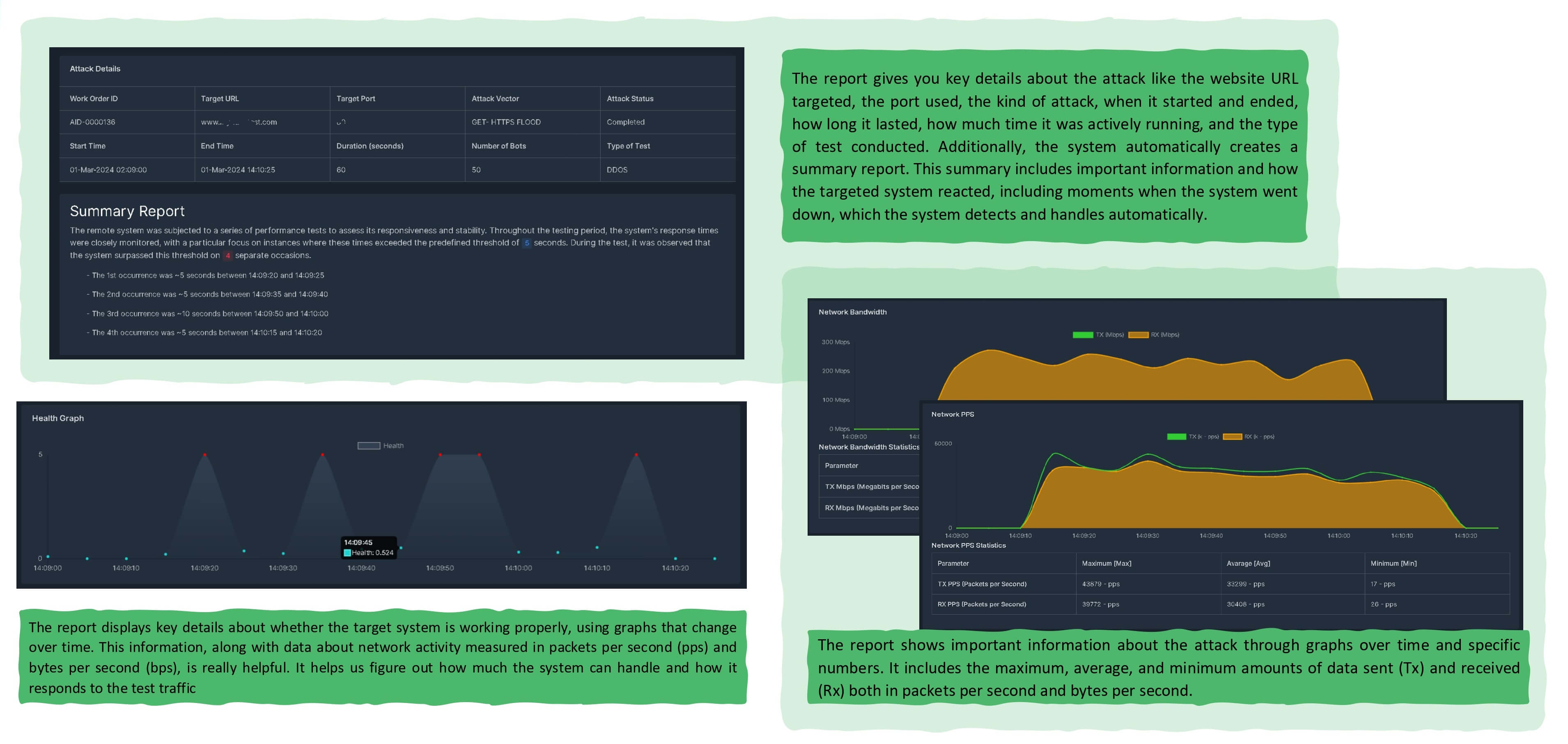
Safedash system has 3 different type of reports
1- Online reporting durinng attacks
2- Offline report right after the ddos attack
3- Detail report (if needed)
1- Online reporting durinng attacks
2- Offline report right after the ddos attack
3- Detail report (if needed)
1000+ BOTs
200+ Gbps
A distributed denial-of-service (DDoS) attack refers to a malicious player that disturbs the regular flow of traffic to a specific server, service, or network.
This disruption is caused by inundating the target or its connected infrastructure with excessive Internet traffic. DDoS attacks are harnessed by utilizing numerous compromised computer systems as sources of the attacking traffic. These compromised systems can encompass traditional computers and other interconnected resources like Internet of Things (IoT) devices.
At a conceptual level, a DDoS attack bears resemblance to an unanticipated traffic congestion
that congests a highway, impeding the regular progression of traffic towards its intended
destination.
One of the primary challenges in identifying a DDoS attack lies in the familiarity of its symptoms. Many of these indicators closely resemble the experiences of regular technology users, such as sluggish upload or download speeds, websites becoming temporarily unavailable, intermittent internet connectivity, unusual content or media, or an upsurge in spam. Additionally,
the duration and intensity of a DDoS attack can vary significantly, ranging from a few hours to several weeks – this is what is referred to as downtime.
DDoS attacks are executed through networks comprising interconnected Internet-enabled machines. These networks encompass computers and various devices (including Internet of Things devices) that have been compromised by malware, enabling remote control by an attacker. These individual compromised devices are termed “bots” or “zombies,” while a collection of such bots forms a “botnet.” Once a botnet is established, the attacker can orchestrate an assault by issuing remote commands to each bot within the network.
Upon targeting a victim’s server or network, each bot within the botnet sends requests to the target’s specific IP address. This onslaught of requests has the potential to overwhelm the server or network, resulting in a denial of service for legitimate traffic. The intricacy arises from the fact that each bot in the botnet is a genuine internet-connected device. Thus, distinguishing between the malicious attack traffic and the normal traffic becomes a complex task.
Reporting – Once testing is completed, a DDoS Test Report is created that highlights points of strengths and weaknesses of your DDoS attack handling, and recommendations for further action.
Yes it is.
Not only do many Fortune 500 and large organizations regularly use DDoS Testing, but in some
countries, DDoS Test has become a recommended regulation for validating the organization’s
human response and procedural handling to DDoS attacks.
Start your partner journey
Fill out our online form or give us a call to begin your partnership journey and find out why RPM partners consider us the top IT reseller platform in the UK.


Countries Wordwide
- let's build tomorrow together
About Safedash
At Safedash, we are unwavering in our commitment to fortifying your digital landscape against an array of cyber threats. We understand that in today’s dynamic digital environment, businesses face ever-growing challenges that require resilient and adaptable solutions. Our two flagship products, CastDDOS and CastLOAD, are specifically designed to ensure your business remains robust and agile in the face of unexpected digital adversities. Safedash's mission is to empower businesses with cutting-edge tools and resources to confidently navigate the evolving landscape of cyber threats. We aim to simplify the security journey by offering advanced testing tools and easy access to valuable data, enabling businesses to focus on their growth and success.
Hear from trusted clients
 Maria Sanchez
Maria Sanchez  Alex Fernandez
Alex Fernandez  Tom Sanchez
Tom Sanchez Hub IT allows your business and technology computers to store, transmit, analyze, and manipulate big data in the digital world.
Hub IT allows your business and technology computers to store, transmit, analyze, and manipulate big data in the digital world.
Hub IT allows your business and technology computers to store, transmit, analyze, and manipulate big data in the digital world.
Contact us to secure your IT needs.
Let’s collaborate and make an impact with our cross-discipline approach to design and deveopment.