Vendors & Servıces
S3M Security
Basic concepts and terminology of S3M Security NAC
S3M Free NAC
S3M Security's Free NAC Edition is a robust, no-cost solution designed to safeguard networks for businesses with up to 50 users. This edition includes full access to our highly reliable Authentication and Endpoint Protector modules. Its intuitive design and quick deployment process make it an excellent choice for small businesses, medium-sized companies, and enterprises alike. Enhance your network security effortlessly with S3M Security’s Free NAC Edition today.
FREE NAC FAQ
When you download the Freenac download form you will be automatically sent the information to your e-mail address, a corporate e-mail address is required.
Installation instructions will be sent to your e-mail address with the download link.
There is no limit to the duration of the license. It can be used for a lifetime.
The free version is limited to 50 users. You can contact [email protected] for more information.
There is no vendor support in the free version. You can reach [email protected] for support.
Elevate Your Network Security with S3M Security
S3M Security empowers administrators with an efficient, streamlined approach to maintaining robust network security. Our platform offers a concise snapshot of network performance and user activities, enabling proactive security management.
Top Rejected Users
Identifies users who have the highest number of access denials.
Top 10 Usage
Displays the ten users or devices with the most significant data usage
Visibility 360
Provides a comprehensive overview of network activities and status
Last 10 Authentications
Shows the most recent ten authentication attempts, successful or otherwise.
Authentication Status
Offers a summary of recent authentication successes and failures
Data Utilization
Graphically represents how data is being consumed across the network
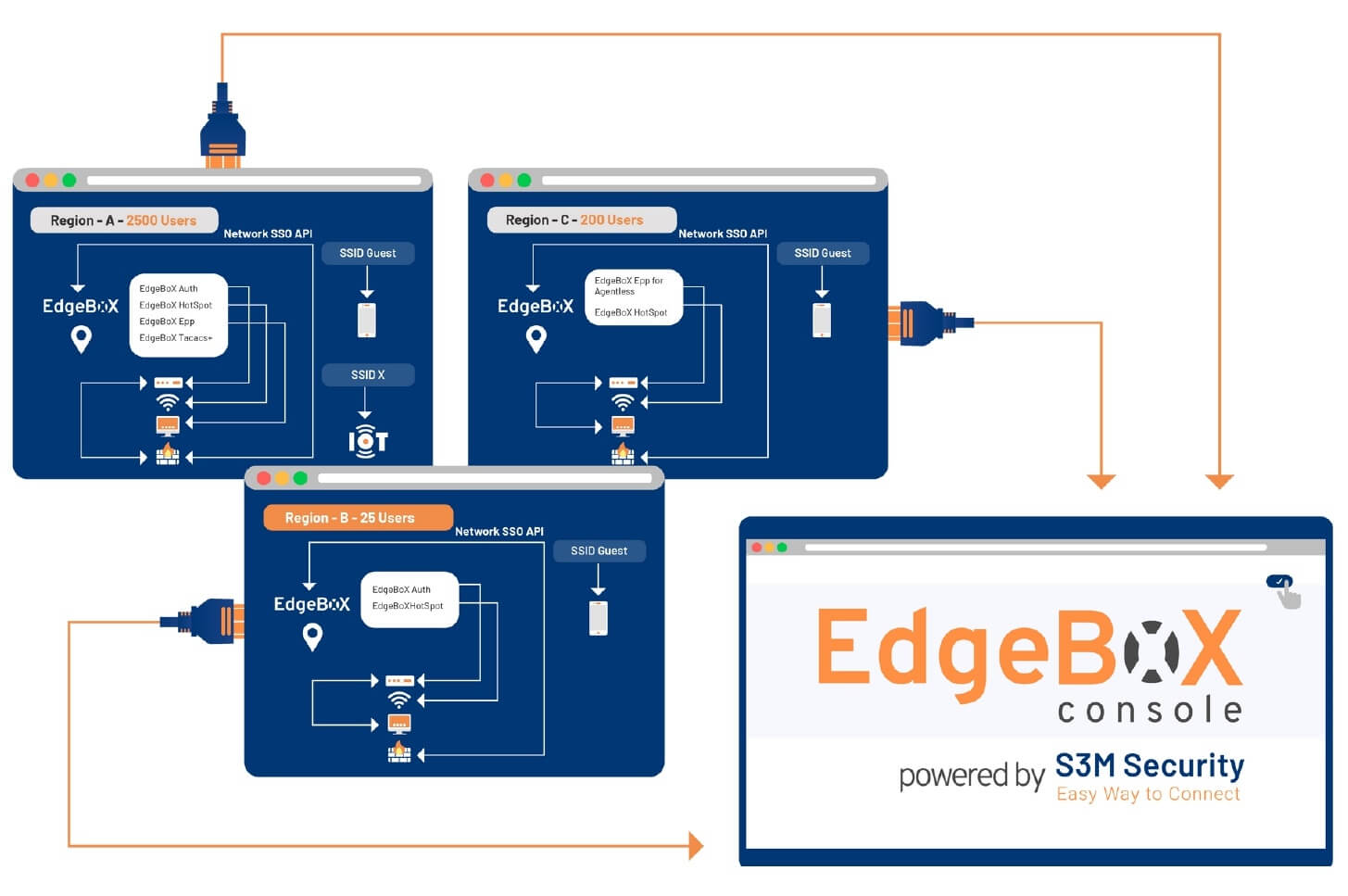
EdgeBoX | MSSP NAC
EdgeBoX is a cyber security solution designed to be used in Managed Security Service Provider (MSSP) activities in organizations with distributed branch infrastructure or centrally managed multi-domain infrastructure and authorizations. It provides radius-based authentication, TACACS+, Hotspot, and agent/agentless NAC service and can be managed by private or public cloud.
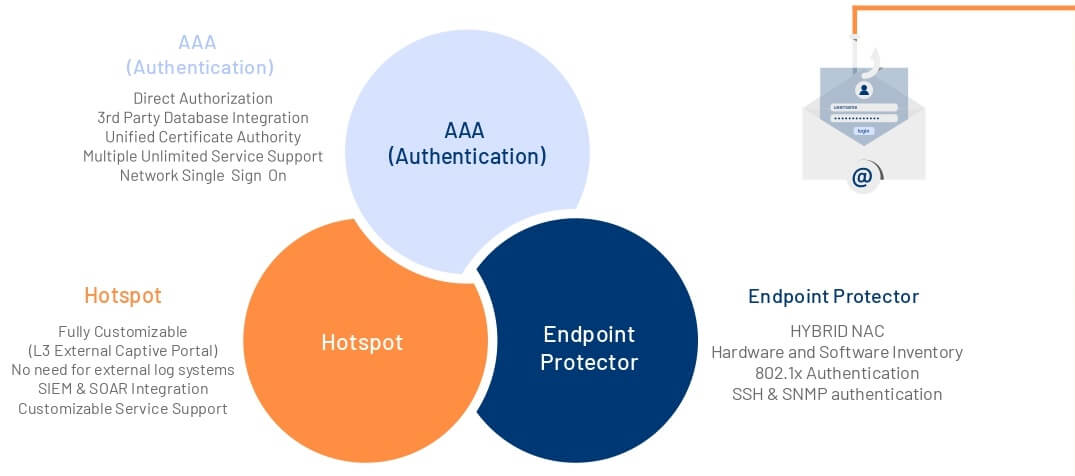
Hotspot
S3M Hotspot module simplifies workflow processes for guest network accesses. Instead of network administrators creating a separate account for each visitor, guests can access the system themselves. Allows guests trying to access to register and authenticate.
Authentication (AAA)
Authentication Module is basically and AAA Radius Management tool that can serve multiple identity resources and network devices with its service and group structure that can run on a single server. It supports standalone or subordinate CA SSL architecture with its built-in Certificate Authority. It can serve instant interventions on live systems .
Endpoint Protector
With EPP Module, it is possible to work without domain dependency in the agent architecture. During the application phase, connection to the remote device is provided with Powershell and SSH. Data collection and editing can be per formed by running WMI, Powershell, SSH and CMD commands. Network access of unsuitable devices can also be changed with dynamic VLAN switching methods from active network devices with SNMP and SSH access.
Network Access Control (NAC) systems play a crucial role in achieving Cyber Essentials Plus
certification by ensuring that only authorized and compliant devices can access your network.:
1. Device Authentication: NAC systems verify the identity of devices attempting to connect
to the network, ensuring that only trusted devices are allowed access. This aligns with
Cyber Essentials Plus requirements for secure access control.
2. Compliance Enforcement: NAC systems can enforce compliance with security policies by
checking devices for up-to-date antivirus software, patches, and configurations before
granting access. This helps meet the Cyber Essentials Plus criteria for maintaining secure
configurations and patch management.
3. Network Segmentation: By segmenting the network, NAC systems limit the spread of
potential threats. This is important for protecting sensitive data and systems, which is a
key aspect of the Cyber Essentials Plus certification.
4. Monitoring and Reporting: NAC systems provide detailed logs and reports on network
access, which are essential for the audit and verification processes required for Cyber
Essentials Plus.
5. Threat Response: NAC systems can automatically respond to detected threats by isolating compromised devices, thereby maintaining the integrity and security of the
network Implementing a robust NAC system can significantly enhance your organization’s security posture and help you meet the stringent requirements of Cyber Essentials Plus certification.
Network Access Control (NAC) works by enforcing security policies on devices attempting to access a network.
Here’s a breakdown of how it operates:
1. Device Identification: NAC identifies devices trying to connect to the network. This can include
laptops, smartphones, tablets, and IoT devices. It uses methods like MAC addresses, certificates, or agent-based software to recognize devices.
2. Authentication: Once a device is identified, NAC authenticates it to ensure it is allowed to access the network. This can involve verifying user credentials, device certificates, or other authentication methods.
3. Compliance Check: NAC checks if the device complies with the organization’s security policies. This includes verifying if the device has up-to-date antivirus software, operating system patches, and other security configurations.
4. Access Control: Based on the authentication and compliance check, NAC determines the level of access the device should have. It can grant full access, limited access, or deny access altogether.
For example, a compliant corporate laptop might get full access, while a personal smartphone
might only get access to the guest network.
5. Monitoring and Enforcement: NAC continuously monitors devices on the network for any
suspicious activity or policy violations. If a device becomes non-compliant or exhibits unusual
behavior, NAC can take actions such as quarantining the device, restricting its access, or notifying administrators.
6. Remediation: If a device is found to be non-compliant, NAC can guide the user through steps to bring the device into compliance. This might involve updating software, installing patches, or
configuring security settings.
By implementing these steps, NAC helps maintain a secure network environment, ensuring that only authorized and compliant devices can access network resources.
Network Access Control (NAC) handles guest devices by providing secure, temporary access to the network while ensuring these devices do not compromise security. Here’s how it typically works:
1. Guest Registration: Guests are often required to register their devices through a self-service
portal. This can include providing personal information and agreeing to the organization’s
terms of use.
2. Authentication: Once registered, guests receive temporary credentials (such as a username and password) to access the network. This ensures that only authorized guests can connect.
3. Compliance Check: NAC performs a compliance check on guest devices to ensure they meet basic security requirements, such as having up-to-date antivirus software and patches2.
Non-compliant devices may be denied access or given limited access.
4. User Experience: Customizable captive portals allow organizations to create a branded and
user-friendly experience. They can include logos, colors, and custom messages that align
with the organization’s branding.
5. Network Segmentation: Guest devices are typically placed on a separate network segment or VLAN. This segmentation ensures that guest devices can only access specific resources,
such as the internet, and are isolated from sensitive internal systems.
6. Monitoring and Enforcement: NAC continuously monitors guest devices for any suspicious activity or policy violations. If a guest device is detected to be a threat, NAC can isolate it from the network or restrict its access.
7. Access Expiry: Guest access is usually time-limited. Once the access period expires, the guest device is automatically disconnected from the network.
By implementing these measures, NAC ensures that guest devices can access the network securely without posing a risk to the organization’s internal resources.
Certainly! A captive portal is a web page that users are automatically directed to when they attempt to connect to a network. This page typically requires users to authenticate themselves or agree to terms of service before they can access the internet or other network resources.
Here’s how captive portals work within the context of Network Access Control (NAC):
1. Redirection: When a user connects to the network, their HTTP traffic is intercepted and
redirected to the captive portal. This happens before they can access any other web pages.
2. Authentication and Registration: The captive portal presents a web page where users must authenticate themselves. This can involve entering a username and password,
registering their device, or agreeing to the network’s terms of service.
3. Compliance Check: The captive portal can also perform compliance checks, ensuring that the user’s device meets the network’s security requirements. This might include checking for up-to-date antivirus software, operating system patches, and other security
configurations.
4. Access Control: Once the user has authenticated and their device has passed the compliance check, the captive portal grants them access to the network. This access can be full or limited, depending on the user’s role and the network’s policies.
5. Monitoring and Enforcement: The NAC system continues to monitor the user’s device
and network activity. If any suspicious behavior or policy violations are detected, the NAC can take action, such as redirecting the user back to the captive portal for
remediation.
Captive portals are commonly used in public Wi-Fi networks, hotels, airports, and corporate guest networks to ensure that only authorized users can access the network and that their devices are secure.
The Endpoint Protector module focuses on securing endpoints, which are often the most vulnerable parts of a network.
1. Device Management: Provides comprehensive control over devices, including remote
control, location tracking, and notifications for hardware changes.
2. Advanced Verification: Uses a two-layer management and verification system to
enhance security and operational efficiency.
3. Command Flexibility: Supports various command interfaces such as WMI, PowerShell,
SSH, and CMD, allowing for versatile data management.
4. Hardware Inventory: Collects and monitors hardware inventory, instantly detecting any
changes in devices on the network.
5. Health Check: Conducts thorough health and posture checks to ensure devices meet
predefined security standards before granting network access.
6. Hybrid NAC Technology: Combines agent-based and agentless structures to leverage
their strengths and provide a robust security framework
These modules work together to provide a secure and efficient network environment, ensuring that only authorized users and compliant devices can access the network.



