Vendors & Servıces
Sechard
All you need for Zero Trust, now in a single platform!
Complete Zero Trust is now possible by ONE!
- Full Cybersecurity Robotic Process Automation
- All features in Security Hardening
- All features in PAM/Tacacs
- All features in Asset Manager
- All features in Operations Manager
- Any new modules/products will be released
- Security Hardening GAP reports for CIS, DISA STIG and CBDDO
- Security Hardening Scoring
- Full Automated Remediation
- 110+ Supported products (network devices, servers, clients, applications, databases, cloud systems, middleware, etc.)
- Compliance Reports for ISO 27001, PCI-DSS, HIPAA, NIST 800-171, NIST 800-53, SoX, CIS Critical Security Controls, CMMC, Turkish CBDDO, Saudi Arabia ECC
- Custom Recipes and Audits
- Automated or Manual Roll Back
- Detailed, historical and delta reports
- Cust
- Central and Personal Password Vaults
- Session Management and Recording (RDP, VNC, SSH, Telnet, Web browser, etc.)
- OCR Support for video record indexing
- Just in Time Access
- Role Management
- Active Directory Bridging
- Command Blocking
- Active Directory Dynamic Group Mapping
- Tacacs, Tacacs+ and Radius Servers
- 3+ Nodes Active-Active clustering
- MFA Support (SecHard, Microsoft, Google, SecurifyID supports
- Automatic Asset Discovery (AD, VMware, HyberV integrations and network scan)
- Hardware/Software Inventory Management
- SSL Key discover, analysis and management
- Asset Risk Scoring for ISO 27001, NIST CSF and other regulations (Risk=Impact X Probability)
- Asset Check in/Check out
- Inventory Change/Integrity Monitoring
- High Risk Triggers (Triggering to change third party cybersecurity product configurations. Ex: Trellix)
- Risk Dashboards and Reports
- Network Device Configuration Backup/Restore
- Configuration Integrity Control
- Performance Monitoring for Servers, clients, network devices, applications and more
- Automated Network Map Visualizing
- Bulk Command Sending
- Firmware Upgrades
- Network Device Vulnerability Reporting
- Server and clients Vulnerability Reporting (coming soon)
- Syslog and SNMP Automation
SecHard Zero Trust Orchestrator
SecHard Zero Trust Orchestrator is an advanced, fully automated software solution capable of conducting security analysis and implementing necessary remediations without expert intervention. This approach enhances organizational security and delivers an exceptional return on investment.

Security Hardening
SecHard offers automated security hardening solutions that include auditing, scoring, and remediation for servers, clients, network devices, applications, databases, and other critical IT infrastructure components.

Privileged Access Manager
A robust identity and access management software designed to ensure Zero Trust compliance and protect against threats such as privilege abuse, ransomware, and other cyberattacks.

Asset Manager
SecHard addresses the challenges of risk awareness in asset management by offering automated discovery, access, identification, and remediation features. These capabilities ensure comprehensive visibility and compliance across all regulatory requirements.

Vulnerability Manager
SecHard utilizes a passive scanning method to conduct vulnerability detection and management for all IT assets, ensuring no additional risks are introduced during the process.

Key Manager
SecHard automatically discovers certificates within your company's environment, reports their expiration dates, and offers automatic renewal for select certificates through trusted certificate authorities.

Risk Manager
SecHard's unique risk assessment formula calculates real-world risk scores by integrating asset group risk scores, security hardening scores, and vulnerability scores.

Device Manager
Comprehensive and customizable network device management featuring backup and restore, configuration change detection, performance monitoring, bandwidth monitoring, and firmware upgrades.

Performance Monitor
Unified performance and availability monitoring for servers, network devices, databases, applications, IoT, and industrial control systems.

TACACS+ Server
Centralized Authentication, Authorization, and Accounting (AAA) for *nix systems and network devices with seamless Microsoft Active Directory integration.

Syslog Server
Streamlined log management for network devices and servers, featuring real-time alerts for critical events and log forwarding in Syslog and CEF formats.
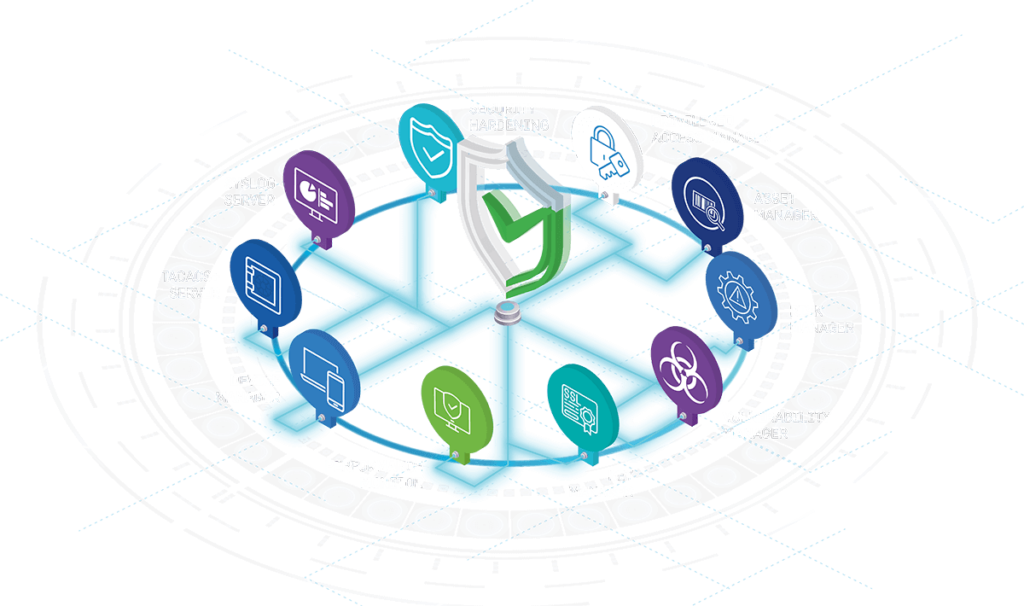
SecHard Zero Trust Orchestrator
SecHard is a multi-module software for implementing Zero Trust Architecture. This game-changer product facilitates compliance with the Executive Office of Presidential memorandum, NIST SP 800-207, and Gartner Adaptive Security Architecture.
Security Hardening
SecHard offers comprehensive automated security hardening, auditing, scoring, and remediation for a wide range of IT assets, including servers, clients, network devices, applications, and databases. According to CIS, securing a Microsoft Windows Server requires adjusting around four hundred security settings from their default state. Enterprises often face hundreds of missing security settings across their computers, and manually addressing these issues in large networks can be a time-consuming process. SecHard simplifies this by allowing organizations to integrate custom controls and apply them across thousands of assets effortlessly. This enables tailored audits and automated remediations for a diverse array of technologies, including Operating Systems, Network Devices, Applications, IoT, SCADA, Swift, POS, and more, streamlining security management and significantly reducing the workload for IT teams.
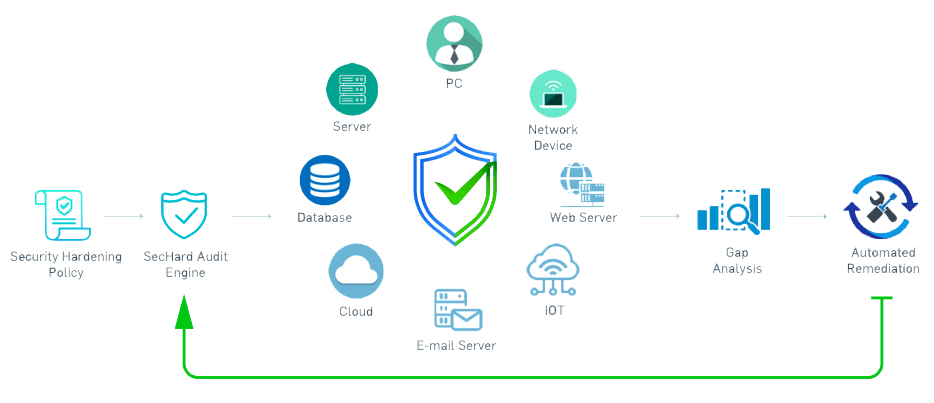
SecHard Zero Trust Orchestrator is a comprehensive multi-module software solution designed to implement Zero Trust Architecture effectively. It is a transformative tool that helps organizations comply with key standards and guidelines, including the Executive Office of the President's memorandum, NIST SP 800-207, and Gartner's Adaptive Security Architecture framework.
SecHard streamlines security hardening by providing automated auditing, scoring, and remediation for a wide range of IT assets, including servers, clients, network devices, applications, and databases. According to CIS guidelines, securing a Microsoft Windows Server requires adjusting around four hundred default security settings. In large enterprise networks, identifying and addressing these security gaps manually can be incredibly time-consuming. SecHard simplifies this by allowing organizations to easily integrate custom controls and apply them across thousands of assets. This automation enables efficient audits and remediations for both common and specialized technologies, such as Operating Systems, Network Devices, IoT, SCADA, Swift, POS, and more, reducing the time and effort required for comprehensive security management.
SecHard simplifies the security remediation process by automating necessary changes with a single click, significantly reducing the time and expertise required. Traditional remediation often demands experienced specialists and can be time-consuming, with critical changes potentially leading to unexpected and disastrous consequences. SecHard addresses these challenges by performing security remediations instantly and accurately, eliminating risks associated with manual changes and the need for in-depth technical knowledge. This automation ensures that security issues are resolved swiftly and safely, enhancing overall system security without the complexities and potential pitfalls of manual remediation.
SecHard employs a passive scanning method to detect and manage vulnerabilities without introducing any risks to your IT assets. By using the asset manager and device manager modules, SecHard collects detailed information about assets and their software. It can also import vulnerability scores from third-party scanning tools to integrate into its risk management process. Additionally, SecHard is capable of sharing its generated information with other third-party software, ensuring a comprehensive and coordinated approach to vulnerability management.
Privileged Access Management (PAM) involves controlling and monitoring the access of authorized users to sensitive data and systems to prevent unauthorized access, misuse, or theft. To effectively manage PAM, organizations should adopt a comprehensive approach that integrates technology, processes, and people. This includes assessing the current PAM maturity level, identifying gaps and risks, and developing a roadmap for improvement. Engaging all relevant stakeholders—such as IT, security, compliance, and business units—is crucial to ensure everyone understands their roles and responsibilities. Organizations should also select a PAM solution that meets their needs and budget, focusing on features like privileged session management, password vaulting, credential rotation, access request workflows, and audit trails, as well as ensuring compatibility with other security and IT management tools.
Start your partner journey
Fill out our online form or give us a call to begin your partnership journey and find out why RPM partners consider us the top IT reseller platform in the UK.
Contact us to secure your IT needs.
Let’s collaborate and make an impact with our cross-discipline approach to design and deveopment.

1. Top Rejected Users: Identifies users who have the highest number of access denials.
2. Top 10 Usage: Displays the ten users or devices with the most significant data usage.
3. Visibility 360: Provides a comprehensive overview of network activities and status.
4. Last 10 Authentications: Shows the most recent ten authentication attempts, successful or otherwise.
5. Authentication Status: Offers a summary of recent authentication successes and failures.
6. Data Utilization: Graphically represents how data is being consumed across the network.
Basic concepts and terminology of S3M Security NAC

The AAA framework, standing for Authentication, Authorization, and Accounting, is integral to network security, providing secure access to network resources. Authentication represents the initial step a user undergoes to gain system access, establishing their identity.

Facilitates the management of wifi access to the network, providing a secure and controlled internet access enables organizations to control guest users.

In the context of network security, EPP is a methodology that protects orporate data when accessed by desktops, aptops, mobile devices, and other endpoints connecting to the enterprise network. Each device poses a potential security risk. Endpoint Protection comprises a uite of solutions aimed at securing these network-connected devices.


Enhanced Network Security
The 2021 release of our software introduced the Network Single Sign-On (SSO) feature, integrating with leading firewalls including Fortinet, Checkpoint, Palo Alto, and Sophos. This innovation allows for unified access to network resources through a single authentication process, sending the user information directly with firewalls. Additionally, the latest version supports hybrid architecture, providing functionality in both agent-based and agentless environments. In 2022, Hybrid NAC's capacity is expanded to accommodate up to 50,000 users per server.
Empowering Global Network Security
S3M Security Hybrid NAC is a unique Hybrid NAC solution designed to meet the common needs and expectations of all MSPs and Resellers. Despite the diversity in customer requirements, it can work either at the customer location (on-premise) or by deploying NAC as a service (CLOUD/MSP Partner Datacentre) to meet the basic demands in terms of security and operational efficiency.
Hybrid NAC integrates key components such as access management, comprehensive network visibility, customized reporting, and remediation capabilities, ensuring your network remains both secure and efficient. This suite of comprehensive services designed to protect and empower your network and information systems across the USA, Europe, EMEA, and Asia, our reach is as extensive as our commitment is deep.
With a track record spanning over nine years, S3M Security has empowered over 100,000 endpoints, small and medium-sized enterprises (SMEs) to enhance their network security and efficiency. Our expertise in network security and auditing has positioned us as a trusted partner in 38 countries worldwide, supported by a dedicated team of 68 professionals.
The 2021 release of our software introduced the Network Single Sign-On (SSO) feature, integrating with leading firewalls including Fortinet, Checkpoint, Palo Alto, and Sophos. This innovation allows for unified access to network resources through a single authentication process, sending the user information directly with firewalls. Additionally, the latest version supports hybrid architecture, providing functionality in both agent-based and agentless environments.
In 2022, Hybrid NAC's capacity is expanded to accommodate up to 50,000 users per server.
Hear from trusted clients
 Maria Sanchez
Maria Sanchez  Alex Fernandez
Alex Fernandez  Tom Sanchez
Tom Sanchez Hub IT allows your business and technology computers to store, transmit, analyze, and manipulate big data in the digital world.
Hub IT allows your business and technology computers to store, transmit, analyze, and manipulate big data in the digital world.
Hub IT allows your business and technology computers to store, transmit, analyze, and manipulate big data in the digital world.
1. Security
Enhanced Network Security
The 2021 release of our software introduced the Network Single Sign-On (SSO) feature, integrating with leading firewalls including Fortinet, Checkpoint, Palo Alto, and Sophos. This innovation allows for unified access to network resources through a single authentication process, sending the user information directly with firewalls. Additionally, the latest version supports hybrid architecture, providing functionality in both agent-based and agentless environments. In 2022, Hybrid NAC's capacity is expanded to accommodate up to 50,000 users per server.
2. privacy
Empowering Global Network Security
S3M Security Hybrid NAC is a unique Hybrid NAC solution designed to meet the common needs and expectations of all MSPs and Resellers. Despite the diversity in customer requirements, it can work either at the customer location (on-premise) or by deploying NAC as a service (CLOUD/MSP Partner Datacentre) to meet the basic demands in terms of security and operational efficiency.
Hybrid NAC integrates key components such as access management, comprehensive network visibility, customized reporting, and remediation capabilities, ensuring your network remains both secure and efficient. This suite of comprehensive services designed to protect and empower your network and information systems across the USA, Europe, EMEA, and Asia, our reach is as extensive as our commitment is deep.
With a track record spanning over nine years, S3M Security has empowered over 100,000 endpoints, small and medium-sized enterprises (SMEs) to enhance their network security and efficiency. Our expertise in network security and auditing has positioned us as a trusted partner in 38 countries worldwide, supported by a dedicated team of 68 professionals.
The 2021 release of our software introduced the Network Single Sign-On (SSO) feature, integrating with leading firewalls including Fortinet, Checkpoint, Palo Alto, and Sophos. This innovation allows for unified access to network resources through a single authentication process, sending the user information directly with firewalls. Additionally, the latest version supports hybrid architecture, providing functionality in both agent-based and agentless environments.
In 2022, Hybrid NAC’s capacity is expanded to accommodate up to 50,000 users per server.